The marriage of Prince William to Kate, the Duchess of Cambridge, was streamed live on the British royal family's YouTube channel, the first royal wedding to be covered in such a way.
Livestream, said the event broke its own records, with more than 330,000 viewers at one point.
On Twitter, nine of the top 10 trending topics were related to the royal wedding.
The BBC website, was struggling under the strain Friday morning, intermittently flashing an error message during the ceremony saying the site was experiencing "abnormal traffic".
The two hottest searches on Google were "Royal wedding coverage" and "Kate Middleton wedding dress", (where's pippa ? :) )which devoted the celebrated logo on its home page to the royal wedding and they mapped the royal procession route in 3D.
Palace officials hosted a live multimedia blog on the royal site, where visitors could congratulate the couple in an online wedding book and make donations to the Royal Wedding Charity Fund.
Fears that the global media event, expected to draw two billion viewers worldwide and many of them online could "break" the Internet proved unfounded.
A technology news blog covering mobile phones, software, security, gadgets, and the Internet.
Saturday, April 30, 2011
Live Stream Of Royal Wedding Breaks Internet Records
Libellés :
Associated Press,
Kate Middleton,
Livestream,
Prince William,
Prince William of Wales,
YouTube
How to Dismantle and Destroy a Hard Drive
 There are a ton of reasons why you might want to physically destroy a hard drive rather than use disk wiping software:
There are a ton of reasons why you might want to physically destroy a hard drive rather than use disk wiping software:higher confidence that the data is destroyed, a recourse if your drive has failed and no longer accessible, and sheer fun.
If the thermite method and other extreme physical disposal methods aren't for you, dismantling the drive to get to the platters is an alternative method.
The main process involves removing the screws around the outside of the drive, pulling out the screws holding the electronics, and then popping the cover off.
After removing the magnets, you can get to the platters, the heart of your hard drive.
First run the magnets over the platters to degauss them. Because that's not a guarantee that the data is unrecoverable, you should then physically destroy the platters, bend them or break them with a hammer or saw them into pieces.
And that will be the end of those discs and the data on them.
The video below shows how Google use a disk crushers and the destruction of old hard drives to prevent leakage of customer data.
Libellés :
Data,
Data Recovery,
Disk Management,
Hard disk drive,
hard drive,
Hardware,
Storage
Friday, April 29, 2011
PSN: Credit Card Details For Sale
 This just keeps getting worse by the day, hackers responsible for the PSN breach last week are attempting to sell users' credit card details online.
This just keeps getting worse by the day, hackers responsible for the PSN breach last week are attempting to sell users' credit card details online.They claim to have the details of 2.2m Sony PlayStation Network users, including Credit card security numbers.
They are hoping to sell the credit card list for upwards of $100,000.
Read more here
Libellés :
Credit card,
Hacker,
PlayStation Network,
Security,
Sony,
Sony PlayStation Network
Mortgage, Loan Calculator 1.1 For iPhone
 Mortgage/Loan Calculator 1.1 the latest update for iPhone, iPod touch and iPads is out
Mortgage/Loan Calculator 1.1 the latest update for iPhone, iPod touch and iPads is out Mortgage/Loan Calculator is a new application on the market that offers more flexibility than the other similar apps being offered. This one boasts incredible ease of use coupled with powerful tools for homeowners.
This new application offers incredibly easy to use features that include auto calculating of figures to determine savings of different loan, duration and payment scenarios, factoring in property tax and homeowner's insurance for a complete, comprehensive picture.
Users are also able to email and save results, as well as compare a number of different loan options, side by side.
The app is intuitive and automatically does the work when numbers are entered in the input fields, users don't even have to press a "calculate" button for any of the figuring.
Users are able to very quickly and easily try a number of different scenarios with this application, to determine the impact on their mortgage of making pre-payments or extra ad-hoc payments.
Also they can adjust loan duration periods and monthly payments to see what the financial outcome would be. Homeowners can then plan their loan strategies better by knowing how many extra payments would pay off their mortgage within a desired amount of time.
Or at least they know how much total interest they are paying over the life of the loan, or how much they could save by paying it off early.
To ensure that the figures are accurately comprehensive, the app allows users to factor in their property taxes and insurance to get a truly complete picture of their mortgage costs.
Mortgage/Loan Calculator 1.1 is available worldwide exclusively through the App Store in the Finance category.
Speech to Text Recognition For Google Chrome
 Chrome browser version 11 has a cool new feature:
Chrome browser version 11 has a cool new feature:speech input through HTML.
This means that you can now talk into your microphone and order commands on websites that support the new speech API.
Only limited to Google Translate at the moment and in the English language.
The use the speech feature first make sure that you have a microphone hooked to your computer and using Chrome 1
Next, go to Google Translate and change the “From” language from “Detect language” to “English”.
You should now see a microphone icon appearing at the lower-right corner of the input box.
Click the microphone icon and speak what you want translated. When you're done talking, Google will automatically translate the spoken words. You can even click on the “Listen” button to hear the translated words spoken back to you.
Other sites where you can test the new speech feature is Web2Voice and HTML5 demos.
Libellés :
Google,
Google Chrome,
Google Translate,
HTML5,
Microsoft Speech API,
Speech recognition
TomTom Sold User Data To Police for Speed Traps
 Basically, if you own a TomTom GPS and you got a ticket in a speed trap...it was your own data that busted you!
Basically, if you own a TomTom GPS and you got a ticket in a speed trap...it was your own data that busted you! Here is a statement from TomTom's CEO claiming the company didn't know about this and that it won't happen again:
Libellés :
Global Positioning System,
GPS navigation device,
Harold Goddijn,
Netherlands,
Speed limit enforcement,
TomTom
Thursday, April 28, 2011
Locate Your Camera’s Photos On The Web
 Digital cameras store the camera’s serial number in the photo’s EXIF information, which can then be used to identify photos taken with that specific camera.
Digital cameras store the camera’s serial number in the photo’s EXIF information, which can then be used to identify photos taken with that specific camera.A new web service called "Stolen Camera Finder" uses this concept to locate photos on the Internet.
The main idea behind the search is that the thief may have uploaded photos taken with the camera to the Internet, which would then open up possibilities to identify the person responsible for stealing the digital camera.
You can upload a photo taken with a particular camera to the service’s website, or enter the camera’s serial number directly to start a search for photos on the web.
The drag and drop upload is currently only working under Firefox and Google Chrome, if you use another browser you need to enter the camera’s serial number into the form.
The service crawls the web for photos with serial numbers and adds all that are found to its database, which currently contains a list of well over one million serial numbers.
The positive thing about this service is that you can identify the person responsible for stealing your stuff, see where your photo's are posted on the web and the negative side is that you can stalk a person with this service...
Check out the website here
Libellés :
Camera,
Digital camera,
Exchangeable image file format,
Google Chrome,
Photograph,
Serial number,
Web service
Wednesday, April 27, 2011
What You Need To Know Right Now About The Sony PSN Hack
name, address (city, state/province, zip or postal code), country, email address, birthdate, PlayStation Network/Qriocity passwords and login, handle/PSN online ID.
Note that the email addresses, logins and passwords also have been stolen from Sony
This is going to turn ugly considering that many users on the web use the same email and password combination on a lot of sites.
If you are a customer you need to immediately change your passwords on site where you may have used the same password, and your email account.
Furthermore Sony says that it is possible that profile data may have also been obtained, which would include purchase history and billing address. Worse, they cannot eliminate the possibility that created card data was taken as well.
That’s the worst case scenario, and there is not lot that users of the network can do at this time, but to actively monitor their credit card bills to check for unauthorized payments.
To protect against possible identity theft or other financial loss, remain vigilant to review your account statements and to monitor your credit or similar types of reports.
The data stolen could also be used in custom attacks as the attackers could use the user’s name and other information to make requests look legit.
Sony asks all users to change their PSN passwords as soon as the service goes online again.
A frequently asked questions section has been uploaded to the Playstation website which contains further information and support phone numbers.
With 70 million users, the data alone could be worth a fortune on the black market.
Final note:
1 - PSN users need to change their web account passwords immediately.
2 - You need to change the password of your email accounts if identical
3 - Monitor your credit card statements and account statements to make sure that no unauthorized payments are made from the accounts.
Libellés :
Credit card,
Email address,
Password,
PlayStation Network,
Qriocity,
Sony
Windows Phone 7 Also Collects Location Data
 Image by clintonjeff via FlickrAfter Google and Apple now Microsoft has admitted that Windows Phone 7 tracks users locations.
Image by clintonjeff via FlickrAfter Google and Apple now Microsoft has admitted that Windows Phone 7 tracks users locations.Microsoft revealed that it collects data such as the signal strength, the radio type, and if GPS is available also logs latitude, longitude, direction and speed and also the BSSID, which is the MAC address of the device.
Microsoft said it does not collect information sent over private, non-protected wireless networks. It said that its software specifically only picks up publicly broadcast data from WiFi access points and that packets sent over encrypted or unencrypted networks remain safe from its location tracking.
They reassured customers that it does not collect emails, passwords or similar information from open networks. It also does not monitor devices connected to access points, nor the SSID name of an access point, which could reveal the identiy of the user since many people name their networks with personal information.
Microsoft said that it does not share the data with mobile operators.
Microsoft also stressed that users can turn off this location tracking feature
Many of these questions are likely to be similar to those asked by US lawmakers recently as they probe Microsoft and a number of other companies about their location tracking policies. The fact that Microsoft is publishing the information for all to see might go down well with investigators, as the company apparently is tackling the problem head on.
Libellés :
Apple,
Global Positioning System,
Google,
IPhone,
MAC address,
Microsoft,
Wi-Fi,
Windows Phone 7
Tuesday, April 26, 2011
Calculate And Track Your Gas Mileage
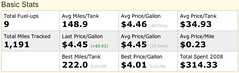 Image by chiaraogan via FlickrFuelly is a handy little web application that's easy to use from your smartphone, or your computer.
Image by chiaraogan via FlickrFuelly is a handy little web application that's easy to use from your smartphone, or your computer.It tracks your gas purchases and mileage over time and calculates miles per gallon overall and per tank.
The best part about Fuelly is comparing your car to others of the same make and model.
Check out the website
XPS File Support For Sumatra PDF Reader
 Image via WikipediaSumatra, the popular lightweight pdf reader has been updated to Version 1.5 and now supports XPS documents (XML Paper Specification).
Image via WikipediaSumatra, the popular lightweight pdf reader has been updated to Version 1.5 and now supports XPS documents (XML Paper Specification).Sumatra 1.5 furthermore adds support for the two popular comic book formats CBZ and CBR which can now be opened and read directly in the application.
Sumatra is only compatible with the Windows operating system.
New users should take a look at the manual which lists helpful keyboard shortcuts, command line options and browser plugin information. A browser plugin for Firefox, Chrome and Opera is included in the full installer of Sumatra, and not in the portable version.
You can download Sumatra PDF Reader Here
Libellés :
Adobe Acrobat,
Chrome,
Microsoft Windows,
Portable Document Format,
Sumatra PDF
iPhone Tweetdeck 2.0 Released
 Image via CrunchBase
Image via CrunchBasePopular Twitter client Tweetdeck is a popular cross-platform Twitter client based on Adobe AIR technology and one of the more useful clients for selective Twitter users, they released a new version for iOS devices, and is completely rebuilt from the ground up to be faster, sleeker, and more efficient.
The app's navigation seems to have been through a major overhaul.
Tweetdeck 2.0 is a free app for devices running iOS 4.0 or later, and is available at the iTunes App Store. Tell us what you think of TweetDeck's "re-imagining" in the comments.
Find out more at the Tweetdeck blog
The Facebook Send Button. What Does It Do?
 Facebook has a new button. It is called Facebook Send .
Facebook has a new button. It is called Facebook Send . Facebook Send allows you to send a web page or message to select friends, groups or email addresses. That’s different from Like which posts the message to all Facebook friend’s on the profile wall.
With Facebook Send, you could send your tech interested friends a new review of a cool tech gadget.
A click on the Send button on a website triggers either a Facebook login, if you are not logged in already, or a small sharing window where you can add recipients at the top and a message at the bottom.
Website owners who already use a Facebook Like button on their website can add the attribute send=true to the code to add the Send button next to the Like button.
It is furthermore possible to create a standalone send button and place that on the website.
The code can be generated on Facebook’s Developers website.
What’s your take on the new Send Button?
Libellés :
Facebook,
Like button,
Social media,
Social network,
Website
Iran hit by second computer worm
 Iran has been hit by a second malware attack in addition to the Stuxnet worm that was designed to disrupt nuclear operations.
Iran has been hit by a second malware attack in addition to the Stuxnet worm that was designed to disrupt nuclear operations."Stars" is the second serious computer worm to hit Iran in the past eight months. Late last year, a powerful virus known as Stuxnet targeted the country's nuclear facilities and other industrial sites.
Iranian security personnel are still in the process of investigating the computer worm, Brigadier General Gholam-Reza Jalali, told Iran's Mehr News Agency
“Certain characteristics about the Stars worm have ben identified, including that it is compatible with the (targeted) system and that the damage is very slight in the initial state, and it is likely to be mistaken for executable files of the government,” said Jalali, who heads Iran's Passive Defense Organization, a military unit in charge of combatting sabotage.
Jalali and other Iranian officials have said that Stuxnet managed to affect a limited number of Iran's centrifuges but that damage was contained after the discovery.
There's no evidence researchers outside of Iran have examined the new worm.
Libellés :
Computer worm,
Iran,
Stuxnet
Monday, April 25, 2011
iPhones secretly tracks your movements
 Image via CrunchBaseAccording to security researchers, Apple iPhones and iPads are recording your every move, logging your exact longitude and latitude and stored into a hidden and unencrypted but easily accessible file that can be read by anyone with physical access to the device.
Image via CrunchBaseAccording to security researchers, Apple iPhones and iPads are recording your every move, logging your exact longitude and latitude and stored into a hidden and unencrypted but easily accessible file that can be read by anyone with physical access to the device.The file, which is stored on both the iOS device and any computers that store backups of its data, can be used to reconstruct a detailed snapshot of the user's comings and goings, down to the second
The researchers didn't offer any guidance on how to turn off the movement tracker, but suggested users encrypt backups when syncing devices with iTunes to prevent the data from being read by people who have access to the underlying computer.
But that advice would do nothing to deter those who steal or otherwise obtain an iPhone or iPad.
The data is stored in the /Library/Application Support/MobileSync/Backups/ folder of computers that sync to the iDevice. While most of the folders and files inside contain pseudo-random names, it's possible to unscramble them by examining files called Manifest.mbdb and Manifest.mbdx. With a few more steps, users will extract a database in the SQLite format that's easily read with multiple applications.
The researchers said that locations are tracked by triangulating near-by cellphone towers. That suggests that the movements are tracked even when an iDevice's GPS features are turned off.
Also they have released open-source software that makes the entire process a snap. It also plots the information to a map that shows the movements of the user. While the locations are stored down to the second, the researchers said, their software intentionally reduces the time to weekly increments to make the data less useful to snoops.
Wednesday, April 20, 2011
Disposable Email Service That Automatically Clicks Activation Links
MailNesia, A new free, temporary email service has just been launched.
Like other services of this type, MailNesia allows you to create disposable email addresses on-the-fly for the purpose of registering on websites and forums, or for any correspondence where you don't want to reveal your real email ID.
Most websites send emails with an activation link to the address you put in during registration on the site. The user has to open the mail and click on the link to verify that the email ID is valid and that the user is indeed the owner of the given email ID.
What is fabulous about MailNesia is that it can automatically open mails and click on activation links thereby completing the account registration process on its own.
When you register on a website that require you to click on activation links, enter a made up MailNesia email ID such as megusta707@MailNesia.com. Wait for a few seconds to give time for the website to send the activation email to the MailNesia address, then simply proceed to the login page and sign-in.
Check it out here
Like other services of this type, MailNesia allows you to create disposable email addresses on-the-fly for the purpose of registering on websites and forums, or for any correspondence where you don't want to reveal your real email ID.
Most websites send emails with an activation link to the address you put in during registration on the site. The user has to open the mail and click on the link to verify that the email ID is valid and that the user is indeed the owner of the given email ID.
What is fabulous about MailNesia is that it can automatically open mails and click on activation links thereby completing the account registration process on its own.
When you register on a website that require you to click on activation links, enter a made up MailNesia email ID such as megusta707@MailNesia.com. Wait for a few seconds to give time for the website to send the activation email to the MailNesia address, then simply proceed to the login page and sign-in.
Check it out here
Tuesday, April 19, 2011
How Web Accounts Get Hacked
Hacking into an e-mail, Twitter, Facebook, or other account is illegal everyone knows that.
Talented individuals with advanced knowledge are not a threat, You are your own threat.
This is a short list of simple things you may not think about. In each, an opportunity is created… one you want to avoid. The idea is to tell you what not to do and why.
Some advanced methods, like phishing, are a bit more complicated than what is covered here.
1. Recovery E-mail Accounts Can Expire
A recovery e-mail account is method a lot of systems use to help you get back into an account that you have lost the password for. The idea is simple. You ask the site to send you your password (some will just reset it). The site says: “Sure dude, it’s been e-mailed to you.” As long as you have access to that other account, you are just fine and dandy.
Check your recovery e-mail account every three months or so. If you do not, the account may be deleted. Someone else can now claim it. If someone claims that account accidentally and you reset your password, then you just lost control of your main account. If it was on purpose, then the next step is to simply go through the password recovery process.
2. Avoid Duplicate Passwords
An easy way to get hacked is to give a site your e-mail address and then use the same password at that site. The same goes if you use the same user name and password at two or more sites. If the site does not encrypt the password, then there is a huge problem. Anyone who works for the site and has access to this information (or gains it) now has everything they need to log-in to your account.
3. Beware Onlookers
Be paranoid. A person standing behind you as you sign in to a website may not be as casual as they seem. In age where so many phones and MP3 players can record video, they don’t even need to be facing you. If a person sees you enter your password, there is a very good chance they can remember it.
4. Use Public Computers Differently
Watch the settings you use on public computers and always remember to sign out. Be sure to double check this. Most of us have formed habits from using personal computers. We often leave that little box checked “Remember me.” underneath the sign in box. Some may click “Yes” to “Do you want to save this password?” after they log in. Forgetting to click “log off” when a session is finished is common place. This is convenient when it is a personal machine, but disastrous on a public machine. Your account is now as easy for someone else to get into as if it was their own personal machine. There are ways to steal passwords that are saved too.
5. Only Use Trustworthy Computers
Trust the computer you are using as much as you trust the owner. By trust, I refer to both the integrity and the aptitude of the person. For a person who lacks integrity, they may intentionally have software running that records what keys you press (called a “keylogger”). Companies in the U.S. can legally install them on any computer they own. For a person who lacks aptitude, they may unknowingly have spyware on there machine. Spyware can sometimes have the same abilities as a keylogger. In either case, once you use that computer to quick check your FaceBook, your account is compromised. If you used that password for you e-mail or banking, you have a larger problem.
6. Avoid Commonly Used Passwords
Do not use the name of your pet, child, team, favorite color, date, etc. as a password. Never use “password” as a password. Too many people use “123456″ (at least at hotmail and rockyou). All of these are easy to guess. A cracking tool is not required to figure them out.
7. Guard Written Passwords
If you choose to write down a password, protect it like your life savings. Would you leave twenty dollar bills sitting around? Your password is much more valuable than that if it is used for your bank account. Nevertheless, I see passwords siting out in the open. It is not a bad idea to never write down your passwords, but the problems of that are obvious. There is no shame in writing them down, but keep them in a safe place… I’m thinking a safety deposit box at the bank.
Talented individuals with advanced knowledge are not a threat, You are your own threat.
This is a short list of simple things you may not think about. In each, an opportunity is created… one you want to avoid. The idea is to tell you what not to do and why.
Some advanced methods, like phishing, are a bit more complicated than what is covered here.
1. Recovery E-mail Accounts Can Expire
A recovery e-mail account is method a lot of systems use to help you get back into an account that you have lost the password for. The idea is simple. You ask the site to send you your password (some will just reset it). The site says: “Sure dude, it’s been e-mailed to you.” As long as you have access to that other account, you are just fine and dandy.
Check your recovery e-mail account every three months or so. If you do not, the account may be deleted. Someone else can now claim it. If someone claims that account accidentally and you reset your password, then you just lost control of your main account. If it was on purpose, then the next step is to simply go through the password recovery process.
2. Avoid Duplicate Passwords
An easy way to get hacked is to give a site your e-mail address and then use the same password at that site. The same goes if you use the same user name and password at two or more sites. If the site does not encrypt the password, then there is a huge problem. Anyone who works for the site and has access to this information (or gains it) now has everything they need to log-in to your account.
3. Beware Onlookers
Be paranoid. A person standing behind you as you sign in to a website may not be as casual as they seem. In age where so many phones and MP3 players can record video, they don’t even need to be facing you. If a person sees you enter your password, there is a very good chance they can remember it.
4. Use Public Computers Differently
Watch the settings you use on public computers and always remember to sign out. Be sure to double check this. Most of us have formed habits from using personal computers. We often leave that little box checked “Remember me.” underneath the sign in box. Some may click “Yes” to “Do you want to save this password?” after they log in. Forgetting to click “log off” when a session is finished is common place. This is convenient when it is a personal machine, but disastrous on a public machine. Your account is now as easy for someone else to get into as if it was their own personal machine. There are ways to steal passwords that are saved too.
5. Only Use Trustworthy Computers
Trust the computer you are using as much as you trust the owner. By trust, I refer to both the integrity and the aptitude of the person. For a person who lacks integrity, they may intentionally have software running that records what keys you press (called a “keylogger”). Companies in the U.S. can legally install them on any computer they own. For a person who lacks aptitude, they may unknowingly have spyware on there machine. Spyware can sometimes have the same abilities as a keylogger. In either case, once you use that computer to quick check your FaceBook, your account is compromised. If you used that password for you e-mail or banking, you have a larger problem.
6. Avoid Commonly Used Passwords
Do not use the name of your pet, child, team, favorite color, date, etc. as a password. Never use “password” as a password. Too many people use “123456″ (at least at hotmail and rockyou). All of these are easy to guess. A cracking tool is not required to figure them out.
7. Guard Written Passwords
If you choose to write down a password, protect it like your life savings. Would you leave twenty dollar bills sitting around? Your password is much more valuable than that if it is used for your bank account. Nevertheless, I see passwords siting out in the open. It is not a bad idea to never write down your passwords, but the problems of that are obvious. There is no shame in writing them down, but keep them in a safe place… I’m thinking a safety deposit box at the bank.
Lastly, remember the first rule of passwords: don’t ever give them out or share them!
Windows 8 New Task Manager Revealed
Images of a new task manager from the leaked Windows 8 has surfaced.
The new task manager is disabled by default
There's a new process list with larger buttons optimized for touch interface.
There's also appears to be considerations made for touch interfaces, as there's a touch-friendly way to kill tasks perhaps for tablet implementations of Windows 8.
The new task manager is disabled by default
There's a new process list with larger buttons optimized for touch interface.
There's also appears to be considerations made for touch interfaces, as there's a touch-friendly way to kill tasks perhaps for tablet implementations of Windows 8.
Piracy as a religion? That is so crazy...
The founders of the Missionary Church of Kopimism, a group of self-confessed radical pirates hopes gaining official recognition of their own unique belief system.
They hold CTRL+C and CTRL+V as sacred symbols – hope that along with this acceptance will come harmony, not just with each other, but also with the police.
Read the full article here and visit the website here
They hold CTRL+C and CTRL+V as sacred symbols – hope that along with this acceptance will come harmony, not just with each other, but also with the police.
Read the full article here and visit the website here
New blog
After getting a lot of positive comments about this blog I decided to make another one about the latest hardwares news from around the world. I hope you will enjoyed this other blog like this blog :)
Here you go the Latest Hardware News
Here you go the Latest Hardware News
Record Internet Radio Stations With Streamwriter
One of the easiest ways to obtain legal music is to record Internet radio.
Tools for the job have evolved a lot over past years, from command line applications to powerful programs that can record dozens of Internet radio stations at the same time.
StreamWriter is such an application. The program has a lot to offer: It can record music from multiple streams at the same time. Even better, it comes with a built-in auto-updating list of Internet radio stations that you just need to click on to start recording.
You can copy and paste a playlist or stream url into the form at the top or use the radio station browser on the right to find suitable radio stations.
You can search for a specific station, or browse stations by genre, quality or file type.
The program will record music for as long as you keep it open and running. You can at anytime stop the recording of an individual station or all stations that are currently being recorded.
Recorded songs are moved to the Saved songs tab where you can play them directly in the application. Another option is to cut recorded music which can be handy to cut off a dj or jingles that have been added to the recording.
The program is available as a installer and portable version
Tools for the job have evolved a lot over past years, from command line applications to powerful programs that can record dozens of Internet radio stations at the same time.
StreamWriter is such an application. The program has a lot to offer: It can record music from multiple streams at the same time. Even better, it comes with a built-in auto-updating list of Internet radio stations that you just need to click on to start recording.
You can copy and paste a playlist or stream url into the form at the top or use the radio station browser on the right to find suitable radio stations.
You can search for a specific station, or browse stations by genre, quality or file type.
The program will record music for as long as you keep it open and running. You can at anytime stop the recording of an individual station or all stations that are currently being recorded.
Recorded songs are moved to the Saved songs tab where you can play them directly in the application. Another option is to cut recorded music which can be handy to cut off a dj or jingles that have been added to the recording.
The program is available as a installer and portable version
Monday, April 18, 2011
What The Power Button Symbol Says
Ever noticed the little symbols that appear on the power button of your device and equipment?
Most people don’t. If it is a toggle switch like the light switch installed on your home and office, you just know which way is ON and OFF since you use them everyday.
If you live in North America, the switch is ON when it is “up” and OFF when “down”. This is reverse in many countries such as the UK, Ireland, India, Australia, and in New Zealand.
Whether you need it or not, all power switches be it is a toggle switch or a push button, have a symbol on it that visually defines how the switch is supposed to work.
The line symbol is usually found in toggle switches connected to the main lines – the typical light bulb switch.
This symbol is found on switches that connects to or disconnects from the mains, with the “OFF” as the stable position, whilst the “ON” position only remains during the time the button is depressed.
This symbol is found on devices that receives power from the mains (or battery) through the power outlet on walls or similar arrangement, such as the computer, monitor, printer or television. A power switch with this symbol does not fully turn off the device as long as it continues to receive power from the source.
Most people don’t. If it is a toggle switch like the light switch installed on your home and office, you just know which way is ON and OFF since you use them everyday.
If you live in North America, the switch is ON when it is “up” and OFF when “down”. This is reverse in many countries such as the UK, Ireland, India, Australia, and in New Zealand.
Whether you need it or not, all power switches be it is a toggle switch or a push button, have a symbol on it that visually defines how the switch is supposed to work.
The line symbol is usually found in toggle switches connected to the main lines – the typical light bulb switch.
This symbol is found on switches that connects to or disconnects from the mains, with the “OFF” as the stable position, whilst the “ON” position only remains during the time the button is depressed.
This symbol is found on devices that receives power from the mains (or battery) through the power outlet on walls or similar arrangement, such as the computer, monitor, printer or television. A power switch with this symbol does not fully turn off the device as long as it continues to receive power from the source.
Grand Theft Auto 5 Release Date January 15th 2012
A Gamestop in Germany has added a release date to their Grand Theft Auto 5 retail listing.
The date stated for the release is set for January 15th of next year.
Take this date as more of a projection and not a confirmed arrival.
Wait for official confirmation from Rockstar games especially during the dates of E3 which is June 7th to June 9th.
If there’s no information about Rockstar games, then go ahead and disregard the January 15th date.
You can expect the game to be out next year for sure, but wouldn’t that be something if we found out that the game would be in our hands by this holiday season?
Who out there loves Grand Theft Auto?
What do you think the next game will be like?
Where do you think it will take place?
The date stated for the release is set for January 15th of next year.
Take this date as more of a projection and not a confirmed arrival.
Wait for official confirmation from Rockstar games especially during the dates of E3 which is June 7th to June 9th.
If there’s no information about Rockstar games, then go ahead and disregard the January 15th date.
You can expect the game to be out next year for sure, but wouldn’t that be something if we found out that the game would be in our hands by this holiday season?
Who out there loves Grand Theft Auto?
What do you think the next game will be like?
Where do you think it will take place?
Pope says technology can't replace God
Speaking to a Roman Catholic crowd at a Palm Sunday event, Pope Benedict said that humans have always had a desire to be like God and have accomplished much over the years, such as flight, through the use of technology.
The Pope has said that technology "can't replace God" and that Man will "pay for his pride" if he thinks technology can give him equivalently divine powers.
He said that technology has helped Mankind, but that it has also increased the possibility for evil,
Benedict highlighted recent natural disasters, such as the Japanese earthquake, as evidence that humanity is not all-powerful.
He said that Man needs to "abandon the pride of wanting to become God" if a meaningful relationship with God is to be attained.
The Pope has previously spoken out against advances in technology, including the Internet. Last year he said that the Internet can exacerbate tensions, lead to "intellectual and morale relativism", not to mention the "pollution of the spirit", which we imagine ranks higher than environmental pollution in his list of dangers.
The Pope has said that technology "can't replace God" and that Man will "pay for his pride" if he thinks technology can give him equivalently divine powers.
He said that technology has helped Mankind, but that it has also increased the possibility for evil,
Benedict highlighted recent natural disasters, such as the Japanese earthquake, as evidence that humanity is not all-powerful.
He said that Man needs to "abandon the pride of wanting to become God" if a meaningful relationship with God is to be attained.
The Pope has previously spoken out against advances in technology, including the Internet. Last year he said that the Internet can exacerbate tensions, lead to "intellectual and morale relativism", not to mention the "pollution of the spirit", which we imagine ranks higher than environmental pollution in his list of dangers.
Microsoft is working on getting Windows 8 to boot from a USB stick.
An early beta version of Microsoft's upcoming Windows 8 operating system was leaked last week allowing users to take a peek at some of its features.
One of the most interesting features is Microsoft's Portable Workspace Creator, which allows Windows 8 to run from a USB storage device.
Users are saying that the minimum storage capacity required for a portable Windows 8 setup is 16GB, suggesting that the operating system will need at least that for a standard installation.
The ability to take an installation of Windows 8 around has both pros and cons for enterprises.
The ability to run a complete operating system from a USB drive isn't particularly new. Linux users have been able to do just that for years and these days Linux installation can even be done from a running Windows installation.
It's important to bear in mind that Microsoft often shows off features in early beta releases that do not make the final cut. There's no doubt that Portable Workspace Creator is a handy feature to have, but at this time there's no confirmation about whether it will available only to Windows 8 Enterprise users.
One of the most interesting features is Microsoft's Portable Workspace Creator, which allows Windows 8 to run from a USB storage device.
Users are saying that the minimum storage capacity required for a portable Windows 8 setup is 16GB, suggesting that the operating system will need at least that for a standard installation.
The ability to take an installation of Windows 8 around has both pros and cons for enterprises.
The ability to run a complete operating system from a USB drive isn't particularly new. Linux users have been able to do just that for years and these days Linux installation can even be done from a running Windows installation.
It's important to bear in mind that Microsoft often shows off features in early beta releases that do not make the final cut. There's no doubt that Portable Workspace Creator is a handy feature to have, but at this time there's no confirmation about whether it will available only to Windows 8 Enterprise users.
Sunday, April 17, 2011
Feds indict poker sites, seize domains
Illegal gambling, money laundering, bank fraud charges
The founders of three internet's largest gambling sites have been indicted and charged with bank fraud, money laundering and illegal gambling.
Eleven individuals have been charged in total by the US Department of Justice with running operations that violated the Unlawful Internet Gambling Enforcement Act of 2006.
The authorities have so-far arrested three individuals, all US citizens, and are working with international law enforcement agencies to arrest a further eight US citizens and foreign nationals in connection with the charges.
The individuals face a range of charges with different prison sentences and fines, while the US is also seeking at least $3bn held by the companies.
The feds have seized five domain names and freezing 76 accounts in 14 counties.
According to New York's US Attorney's Office, the companies operated in contravention of the 2006 act on unlawful gaming.
Authorities say those indicted disguised money from US gamblers as payments to hundreds of non-existent online merchants selling items like jewelry and golf balls.
The founders of three internet's largest gambling sites have been indicted and charged with bank fraud, money laundering and illegal gambling.
Eleven individuals have been charged in total by the US Department of Justice with running operations that violated the Unlawful Internet Gambling Enforcement Act of 2006.
The authorities have so-far arrested three individuals, all US citizens, and are working with international law enforcement agencies to arrest a further eight US citizens and foreign nationals in connection with the charges.
The individuals face a range of charges with different prison sentences and fines, while the US is also seeking at least $3bn held by the companies.
The feds have seized five domain names and freezing 76 accounts in 14 counties.
According to New York's US Attorney's Office, the companies operated in contravention of the 2006 act on unlawful gaming.
Authorities say those indicted disguised money from US gamblers as payments to hundreds of non-existent online merchants selling items like jewelry and golf balls.
Download YouTube HD Videos with youtube Snagger.
Everyday users have dozens of options when it comes to downloading videos from YouTube.
From browser extensions over userscripts to standalone software programs that vary in comfort and features.
YouTube Snagger is a standalone application for Windows that can be used to download videos from YouTube.
YouTube Snagger’s interface has been streamlined for quick downloading of videos. You paste a Youtube video url into the form at the top, select the desired video quality (for instance best available or 4096p) and click the Check Video button afterwards. The program tries to pull data from YouTube and either returns the status that the video can be added or that no video has been found. You need to click on Add video to add the video to the download queue.
The things that take it down a notch are the missing YouTube search option, the to many buttons in the interface, no option to play a video from the interface, or at least launch it in the default player, and that downloaded videos do not get removed automatically from the queue.
You can download the latest version of YouTube Snagger from the developers website.
From browser extensions over userscripts to standalone software programs that vary in comfort and features.
YouTube Snagger is a standalone application for Windows that can be used to download videos from YouTube.
YouTube Snagger’s interface has been streamlined for quick downloading of videos. You paste a Youtube video url into the form at the top, select the desired video quality (for instance best available or 4096p) and click the Check Video button afterwards. The program tries to pull data from YouTube and either returns the status that the video can be added or that no video has been found. You need to click on Add video to add the video to the download queue.
The things that take it down a notch are the missing YouTube search option, the to many buttons in the interface, no option to play a video from the interface, or at least launch it in the default player, and that downloaded videos do not get removed automatically from the queue.
You can download the latest version of YouTube Snagger from the developers website.
Find Downloads On Multiple Torrent Sites
When you are searching for a specific torrent sometimes you may use Bittorrent indexers to find it.
Most indexers allow you to search their index, and it happens that you have to visit and search multiple sites before you find the download that you have been looking for.
Torrent Turbo Search is a free Google Chrome extension that can be utilized to search multiple popular Bittorrent websites at once.
The extension supports various sites like ThePirateBay, Isohunt, BTJunkie, Fenopy and a dozen or so others.
It adds an icon to the Chrome address bar on installation that launches a local search form to find downloads on all supported torrent websites.
All you need to do is to enter a search term in the form and hit enter afterwards. The results are listed in tabs. The first tab displays mixed results from all torrent sites that are supported by the search engine, the remaining results from individual sites.
The search appears to support many different torrent search engines, a lot more than are displayed as tabs on the search results page.
The core question is this: Do you really need an extension like Torrent Turbo Search to search for downloads on multiple torrent sites? The answer is no, obviously. You can use one of the existing torrent meta search engines, for instance Metasearch or NowTorrents instead.
Chrome users who are interested in the popular extension can download it from the official Google Extensions repository.
Most indexers allow you to search their index, and it happens that you have to visit and search multiple sites before you find the download that you have been looking for.
Torrent Turbo Search is a free Google Chrome extension that can be utilized to search multiple popular Bittorrent websites at once.
The extension supports various sites like ThePirateBay, Isohunt, BTJunkie, Fenopy and a dozen or so others.
It adds an icon to the Chrome address bar on installation that launches a local search form to find downloads on all supported torrent websites.
All you need to do is to enter a search term in the form and hit enter afterwards. The results are listed in tabs. The first tab displays mixed results from all torrent sites that are supported by the search engine, the remaining results from individual sites.
The search appears to support many different torrent search engines, a lot more than are displayed as tabs on the search results page.
The core question is this: Do you really need an extension like Torrent Turbo Search to search for downloads on multiple torrent sites? The answer is no, obviously. You can use one of the existing torrent meta search engines, for instance Metasearch or NowTorrents instead.
Chrome users who are interested in the popular extension can download it from the official Google Extensions repository.
French hacker and alleged Anonymous member arrested after bragging on TV
How stupid can you be?
A French hacker has bragged about hacking into the systems of a big government contractor on France 2 national TV. in a television program called "Complément d'enquête" (Further investigation).
He said, and demonstrated that he has gained access to computers belonging to the French Army and Thales Group, a French company that provides information systems and services for the aerospace, defense, and security markets.
He also said he sells and uses credit card and bank account data to buy for himself and others various things.
Thales took immediate measures. It said that he had stolen confidential information from its networks and asked for a formal investigation.
How the French police tracked down the hacker - who was presented as "Carl" during the television programme - is unknown.
The producers of the program say that they respect the anonymity of their sources and that they haven't shared his identity with the police. In fact, they claim they did not know that an investigation was ongoing.
"Carl" was arrested on April 7 in Paris. The police discovered on his computer a large number of credit card and bank account data.
He remains in custody until the hearing, and he's facing a various set of charges: data theft, unauthorized access, and organized fraud.
The interesting thing is that the program was actually focusing on the new type of hacker - the hacktivist, and "Carl" claimed he was a member of Anonymous. Whether that's true is hard to determine since there is no list of Anonymous members. The group is not called Anonymous for nothing.
A French hacker has bragged about hacking into the systems of a big government contractor on France 2 national TV. in a television program called "Complément d'enquête" (Further investigation).
He said, and demonstrated that he has gained access to computers belonging to the French Army and Thales Group, a French company that provides information systems and services for the aerospace, defense, and security markets.
He also said he sells and uses credit card and bank account data to buy for himself and others various things.
Thales took immediate measures. It said that he had stolen confidential information from its networks and asked for a formal investigation.
How the French police tracked down the hacker - who was presented as "Carl" during the television programme - is unknown.
The producers of the program say that they respect the anonymity of their sources and that they haven't shared his identity with the police. In fact, they claim they did not know that an investigation was ongoing.
"Carl" was arrested on April 7 in Paris. The police discovered on his computer a large number of credit card and bank account data.
He remains in custody until the hearing, and he's facing a various set of charges: data theft, unauthorized access, and organized fraud.
The interesting thing is that the program was actually focusing on the new type of hacker - the hacktivist, and "Carl" claimed he was a member of Anonymous. Whether that's true is hard to determine since there is no list of Anonymous members. The group is not called Anonymous for nothing.
Saturday, April 16, 2011
The origin of CTRL-ALT-DELETE
You may not have ever thought about it, but the far-too-often-used keyboard combination of Control + Alt + Delete had to have been brought into existence by some random coder at some point in technological history.
The keystroke combo is attributed to David Bradley.
He was one of the original designers of the IBM Personal Computer.
He came up with the idea after growing weary of waiting for the Power-On Self Test (POST) routine to finish during each reboot of his software testing regiment.
We remember the old days of slow hardware and can understand his frustration at the lost time.
He decided to throw in a shortcut that allowed the software to reboot without power cycling the hardware.
The original implementation used CTRL-ALT-ESC, but was later changed so that one frustrated keyboard mash couldn’t accidentally reboot the system.
The keystroke combo is attributed to David Bradley.
He was one of the original designers of the IBM Personal Computer.
He came up with the idea after growing weary of waiting for the Power-On Self Test (POST) routine to finish during each reboot of his software testing regiment.
We remember the old days of slow hardware and can understand his frustration at the lost time.
He decided to throw in a shortcut that allowed the software to reboot without power cycling the hardware.
The original implementation used CTRL-ALT-ESC, but was later changed so that one frustrated keyboard mash couldn’t accidentally reboot the system.
Google Video Closing Down
Before Youtube, Google tried to conquer the video hosting niche with a service that they called Google Video.
When they discovered that they could not compete with Youtube, they bought Youtube and made people forget about Google Video.
The service was not closed down immediately after the Youtube purchase, but it was clearly put on the backseat. Uploads were disabled in 2009 but hosted videos continued to be served.
Google recommends Youtube after finding out that Google Video was not the Internet user’s favorite service.
You could naturally upload the videos to Youtube, which on the other hand raises the question if you should do that, or look for a more reliable hosting solution.
While it is unlikely that Youtube will be closed down in the near future, users would probably have said the very same thing about Google Video.
Alternatives are popular video hosting sites like Dailymotion, Vimeo, MetaCafe or Photobucket.
What about webmasters who have embedded those videos on their websites and blogs?
They need a third party solution to download this videos, or they could try and find the same or a similar video on other video hosting sites.
One of the easiest options to download those videos is to use the Firefox extension Download Helper.
Keep in mind that you have less than 14 days left to download the videos.
Video owners have two additional weeks to download their videos from the video hosting service.
When they discovered that they could not compete with Youtube, they bought Youtube and made people forget about Google Video.
The service was not closed down immediately after the Youtube purchase, but it was clearly put on the backseat. Uploads were disabled in 2009 but hosted videos continued to be served.
Google recommends Youtube after finding out that Google Video was not the Internet user’s favorite service.
You could naturally upload the videos to Youtube, which on the other hand raises the question if you should do that, or look for a more reliable hosting solution.
While it is unlikely that Youtube will be closed down in the near future, users would probably have said the very same thing about Google Video.
Alternatives are popular video hosting sites like Dailymotion, Vimeo, MetaCafe or Photobucket.
What about webmasters who have embedded those videos on their websites and blogs?
They need a third party solution to download this videos, or they could try and find the same or a similar video on other video hosting sites.
One of the easiest options to download those videos is to use the Firefox extension Download Helper.
Keep in mind that you have less than 14 days left to download the videos.
Video owners have two additional weeks to download their videos from the video hosting service.
Skype For Android Security Flaw Exposes Millions Of Users Personal Data
More than ten million users of Skype for Android are vulnerable to a hack that reveals a huge amount of personal data, Android Police reports.
The site uncovered a way hackers might use a rogue app to access personal information stored by Skype including full name, phone number, email address and contact list.
Basically, the app has an SQLite3 database where information is stored, but the files are unencrypted.
Android Police created an app called Skypwned to demonstrate the extent of the problem.
Android Police explains, "I quickly came up with an exploit, and I was in shock at just how much information I could harvest. Everything was available to the rogue app I created, without the need for root or any special permissions."
Skype is investigating the issue.
The site uncovered a way hackers might use a rogue app to access personal information stored by Skype including full name, phone number, email address and contact list.
Basically, the app has an SQLite3 database where information is stored, but the files are unencrypted.
Android Police created an app called Skypwned to demonstrate the extent of the problem.
Android Police explains, "I quickly came up with an exploit, and I was in shock at just how much information I could harvest. Everything was available to the rogue app I created, without the need for root or any special permissions."
Skype is investigating the issue.
Adobe flash player security update
Adobe has released an update for Adobe Flash Player that fixes a critical security issue in the application that had been discovered earlier this month.
The vulnerability, according to Adobe’s information could be exploited to cause a crash on the user system that could allow the attacker to take control of the operating system.
Reports that the vulnerability is actively exploited by embedding specifically prepared Flash files in Word and Excel documents have been confirmed by Adobe.
The easiest way to find out if your Flash Player is up to date is to visit the About Flash page over at Adobe. The currently installed version and the latest version are displayed on that page.
Downloads are provided at the Flash Player Download page or by manually downloading the Flash Player updates from the Flash Player Support Center.
Flash Player versions affected by the vulnerability are the following:
The vulnerability, according to Adobe’s information could be exploited to cause a crash on the user system that could allow the attacker to take control of the operating system.
Reports that the vulnerability is actively exploited by embedding specifically prepared Flash files in Word and Excel documents have been confirmed by Adobe.
The easiest way to find out if your Flash Player is up to date is to visit the About Flash page over at Adobe. The currently installed version and the latest version are displayed on that page.
Downloads are provided at the Flash Player Download page or by manually downloading the Flash Player updates from the Flash Player Support Center.
Flash Player versions affected by the vulnerability are the following:
Adobe Flash Player 10.2.153.1 and earlier versions for Windows, Macintosh, Linux, and Solaris operating systems
Adobe Flash Player 10.2.154.25 and earlier versions for Chrome users
Adobe Flash Player 10.2.156.12 and earlier for Android
Adobe AIR 2.6.19120 and earlier versions for Windows, Macintosh and Linux
Friday, April 15, 2011
VLC Media Player Security Update
VLC developpers have released a new version of the program that patches another security vulnerability in the program.
The built-in update checker does not seem to recognize the new update yet, which means that VLC users need to download the update from the homepage of the project to install the program update manually.
Downloads for all supported operating systems are available on this page.
You can verify the version of VLC by clicking on Help > About in the program interface, or with the keyboard shortcut Shift-F1.
The built-in update checker does not seem to recognize the new update yet, which means that VLC users need to download the update from the homepage of the project to install the program update manually.
Downloads for all supported operating systems are available on this page.
You can verify the version of VLC by clicking on Help > About in the program interface, or with the keyboard shortcut Shift-F1.
Free On-Demand Virus Scanner from Microsoft
Microsoft has released a program called Microsoft Safety Scanner, a free on-demand virus scanner for the Windows operating system. The difference to conventional antivirus software is the fact that it scans the PC but does not add protection to the operating system at the same time.
Most users will probably use the on-demand scanner to verify that their operating system is clean of viruses and other forms of malware. The major benefit of this approach is twofold. First, they can run Microsoft Safety Scanner next to any installed antivirus or security software on the system. This is obviously better than having to uninstall one antivirus program to run another, as there are often incompatibilities or problems involved when running multiple virus scanners on a system.
The second is the ability to scan the system for malicious software without thinking about configuration of the program, or making sure that it is up to date. The software is using virus information from Microsoft’s Malware Protection center.
Microsoft Safety Scanner has been designed with simplicity in mind. The program can be started right after downloading or transferring it to a Windows PC. Only the depths of the scan needs to be selected, everything else is handled automatically by the application.
You can run a quick scan, full scan or customized scan. A quick scan will check the most likely areas on the system for malicious code like viruses, spyware or computer worms. A full scan on the other hand will scan every single file plus the memory and the Registry.
Microsoft Safety Scanner is an on-demand scanner, which means that it is no replacement for active virus protection on the system. It’s aim is to provide additional means to scan a system, nothing more, nothing less.
The scanner has a size of about 70 Megabytes which includes all definition files.
It is not auto-updating and will automatically expire after ten days. That’s a serious restriction that makes the program more or less unsuitable for tech support purposes as it would have to be downloaded every ten days anew.
The program does not seem to require the Microsoft .NET Framework.
You can download Microsoft’s Safety Scanner from the official website over at Microsoft.com
Most users will probably use the on-demand scanner to verify that their operating system is clean of viruses and other forms of malware. The major benefit of this approach is twofold. First, they can run Microsoft Safety Scanner next to any installed antivirus or security software on the system. This is obviously better than having to uninstall one antivirus program to run another, as there are often incompatibilities or problems involved when running multiple virus scanners on a system.
The second is the ability to scan the system for malicious software without thinking about configuration of the program, or making sure that it is up to date. The software is using virus information from Microsoft’s Malware Protection center.
Microsoft Safety Scanner has been designed with simplicity in mind. The program can be started right after downloading or transferring it to a Windows PC. Only the depths of the scan needs to be selected, everything else is handled automatically by the application.
You can run a quick scan, full scan or customized scan. A quick scan will check the most likely areas on the system for malicious code like viruses, spyware or computer worms. A full scan on the other hand will scan every single file plus the memory and the Registry.
Microsoft Safety Scanner is an on-demand scanner, which means that it is no replacement for active virus protection on the system. It’s aim is to provide additional means to scan a system, nothing more, nothing less.
The scanner has a size of about 70 Megabytes which includes all definition files.
It is not auto-updating and will automatically expire after ten days. That’s a serious restriction that makes the program more or less unsuitable for tech support purposes as it would have to be downloaded every ten days anew.
The program does not seem to require the Microsoft .NET Framework.
You can download Microsoft’s Safety Scanner from the official website over at Microsoft.com
Internet Explorer 10 Will Not Support Vista and XP
Microsoft’s upcoming web browser Internet Explorer 10 would not support Windows XP, considering that Internet Explorer 9 did not support the operating system as well. Windows Vista users on the other hand were caught by surprise that their operating system would not be supported by IE10 as well.
Windows Vista users who try to install the platform preview of Internet Explorer 10 get the message that it does not support any operating system earlier than Windows 7.
Does that mean that Internet Explorer 10 will only run on Windows 7?
For now it does, but it will change with the release of Windows 8. It is rumored that Microsoft will ship Internet Explorer 10 with Windows 8, which means that the browser would support both Windows 7 and Windows 8.
What are your thoughts on Microsoft’s decision ?
Windows Vista users who try to install the platform preview of Internet Explorer 10 get the message that it does not support any operating system earlier than Windows 7.
Does that mean that Internet Explorer 10 will only run on Windows 7?
For now it does, but it will change with the release of Windows 8. It is rumored that Microsoft will ship Internet Explorer 10 with Windows 8, which means that the browser would support both Windows 7 and Windows 8.
What are your thoughts on Microsoft’s decision ?
Subscribe to:
Comments (Atom)





















